Apps power nearly every part of our daily lives, helping us shop, communicate, manage money, navigate, and even monitor our health. But behind the convenience of these applications lies a growing concern: many apps collect more data than they need, are poorly maintained, or come with hidden security risks.
Apps power nearly every part of our daily lives, helping us shop, communicate, manage money, navigate, and even monitor our health. But behind the convenience of these applications lies a growing concern: many apps collect more data than they need, are poorly maintained, or come with hidden security risks.
Why App Smarts Matter More Than Ever
Today, being “app smart” isn’t just a tech-savvy trait; it’s a critical habit for protecting your privacy, your data, and your peace of mind. And here’s something most people miss: you can actually check an app’s permissions, developer credibility, and privacy practices before you ever hit download. It’s a simple habit that can make a big difference in keeping your data safe.[/vc_column_text]
[/vc_column][/vc_row]The Hidden Risks Lurking in Everyday Apps
How to Vet an App Before You Download It
Is Your Team Unknowingly Downloading Risky Apps On Company Devices?
Step-by-Step App Vetting Guide
-
Check the Developer Info
Start with the basics—who made the app?
- Open the app store listing and look for the developer’s name.
- Do a quick Google search: Do they have a legitimate website? Have they built other reputable apps?
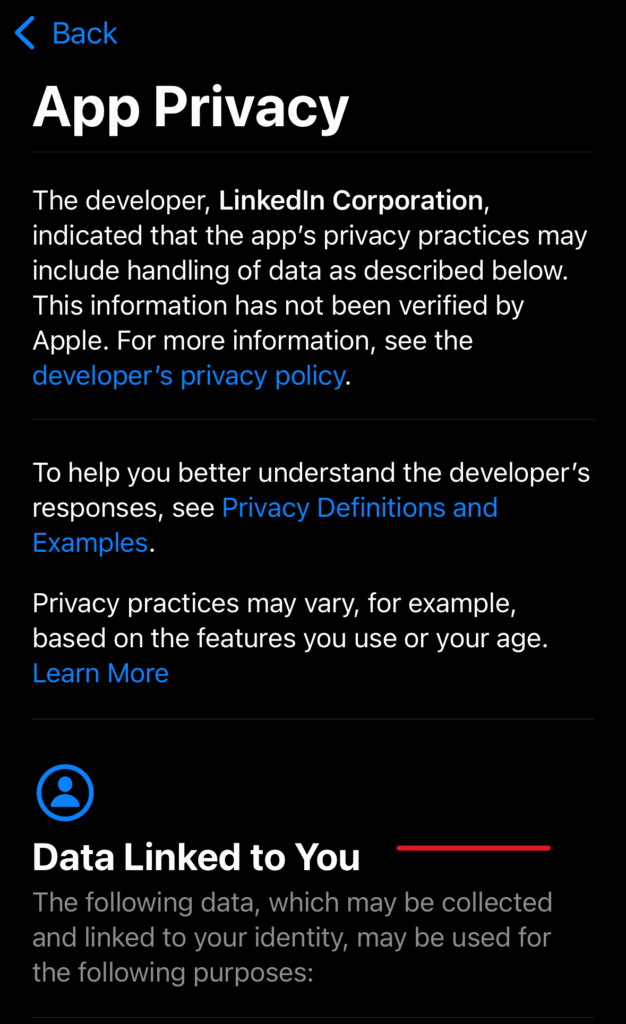
- Look for transparency: contact information, privacy policies, and a regular update history.

-
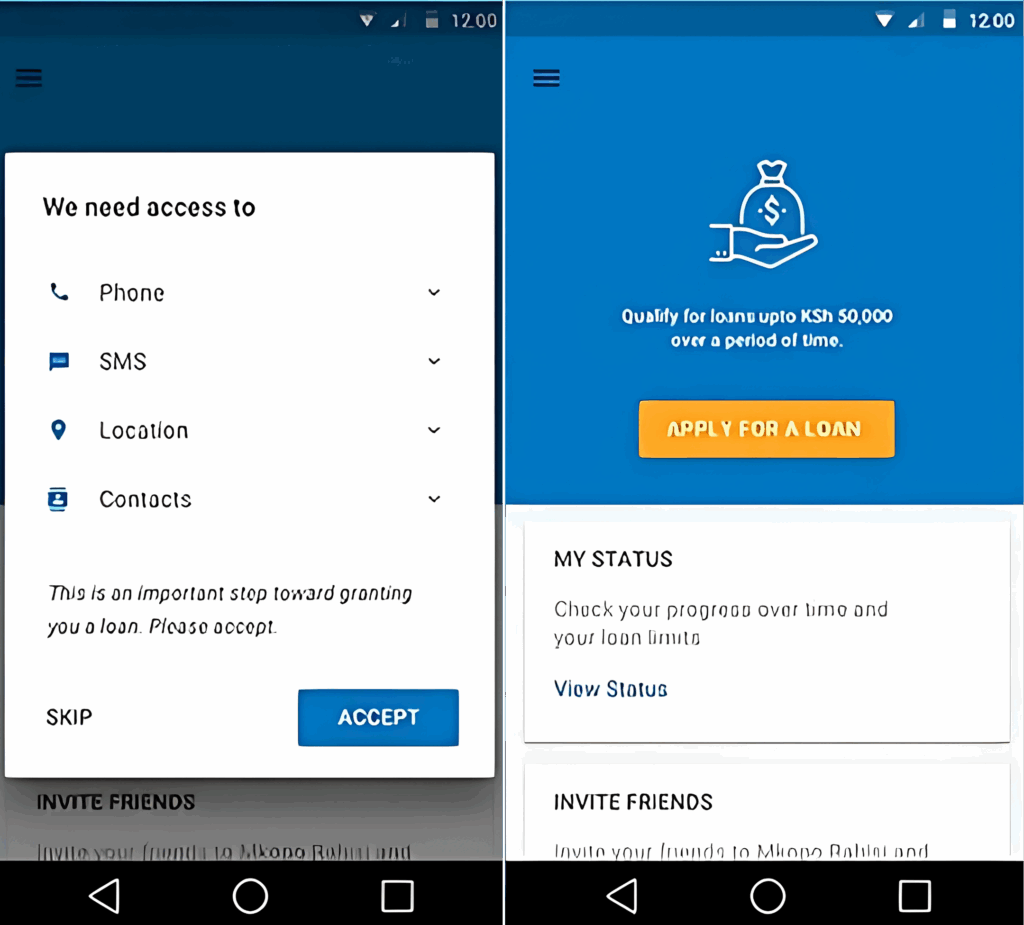
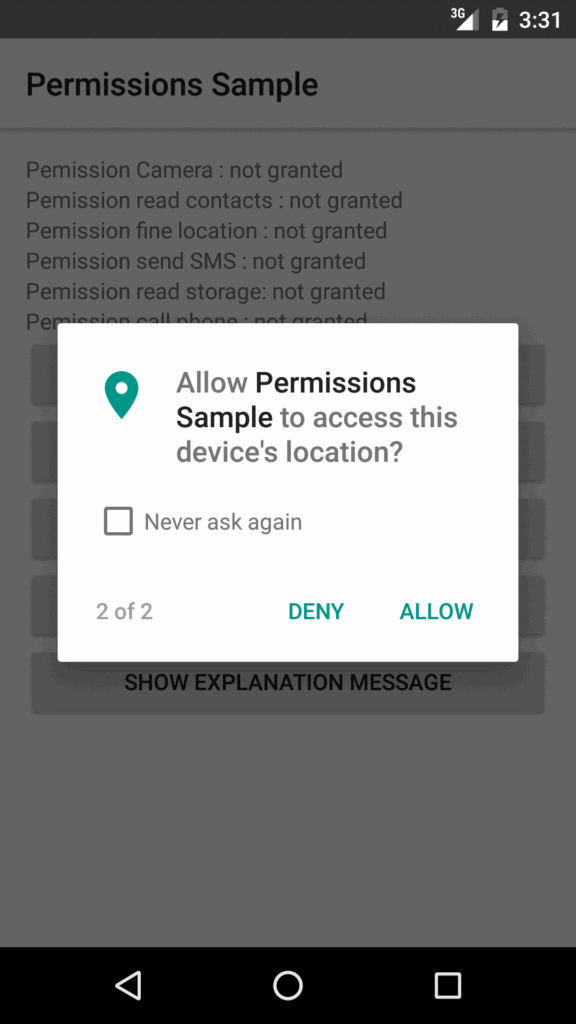
Review App Permissions
Before you install, check what the app wants access to.
- Ask yourself: Does this app really need access to my camera, contacts, or location?
- Be skeptical of unnecessary requests.
-
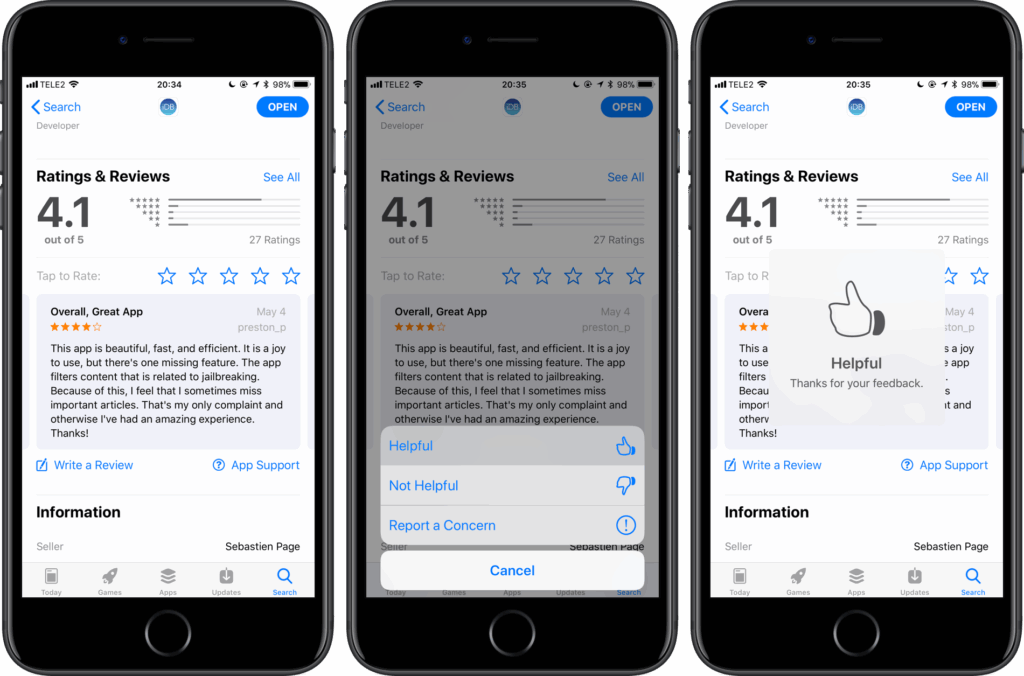
Read User Reviews (the Right Way)
Don’t just skim the 5-star ratings—dig deeper.
- Sort by Most Recent and Critical reviews.
- Watch for patterns: crashes, unexpected data usage, or complaints about shady behavior.
- Use App Safety Tools
For an extra layer of confidence, leverage free tools that analyze apps for risks:
- Exodus Privacy: Reveals trackers inside Android apps.
- AppCensus: Analyzes app behavior and privacy risks.
Be Proactive. Not Reactive.
Being app-smart isn’t about paranoia; it’s about being proactive. Spending just a few minutes researching an app before you download it can protect your personal data, avoid unnecessary risks, and give you peace of mind.
The next time you’re about to install an app, run it through this app privacy checklist, and your future self will thank you.